Sunday, December 27, 2020
Get Guarnateed DA50+ for %domain%
Get an amaazing Domain Authority score above 50 for your website and
increase sales and visibility in just 30 days
https://www.str8creative.co/product/moz-da-seo-plan/
Service is guaranteed
Regards
Mike
Str8 Creative
support@str8creative.co
Wednesday, December 23, 2020
re: I need to make a website`s ranks go down
Yes, it is possible, with our service here
https://negativerseo.co/
for further information please email us here
support@negativerseo.co
thanks
Peter
Monday, December 14, 2020
Our most powerful SEO Ultimate Plan
Getting Top 10 Position in Search Engines is a Must for every Website if
you are really serious to do Online Business. If you are not in top 10 it
means you are getting only 5% of visitors for that particular keyword.
Please find more information on our plan here:
https://str8creative.co/product/seo-ultimate/
thanks
Mike
support@str8creative.co
Tuesday, December 8, 2020
re: Rank top 5 in the Google maps
Did you know that when someone is looking for a search term on their
phones, the Gmaps listings its what pop up first in the results?
Stop losing all that visibility and let us boost your G listing into the
tops for local terms
https://www.str8creative.co/product/1500-gmaps-citations/
thanks and regards
Mike
support@str8creative.co
Friday, December 4, 2020
Buy quality business traffic for blogger.com
Do you want more quality visits engaging on your website?
Increase ranks and sales swith our business website traffic
Please find more information about our service here
https://basedbusinesstraffic.co/
thanks
Peter
Wednesday, December 2, 2020
Guaranteed Domain Authority 50/100
Here is how we can do it
https://www.str8creative.co/product/moz-da-seo-plan/
Regards
Mike
Str8 Creative
support@str8creative.co
Saturday, November 28, 2020
re: I need to make a website`s ranks go down
Yes, it is possible, with our service here
https://negativerseo.co/
for further information please email us here
support@negativerseo.co
thanks
Peter
Saturday, November 21, 2020
Cheap Monthly SEO plans %domain%
After checking your website SEO metrics and ranks, we determined that you
can get a real boost in ranks and visibility by using any of our plan below
https://www.cheapseosolutions.co/cheap-seo-packages/index.html
cheap and effective SEO plan
onpage SEO included
For the higher value plans, DA50 DR50 TF20 SEO metrics boost is inlcuded
thank you
Mike
support@cheapseosolutions.co
Wednesday, November 18, 2020
re: need unique domains backlinks
Do you mean that you want 1 backlinks from 1 domain? unique domains links
like this?
yes, we offer that here
https://str8creative.co/product/unique-domains-links/
thanks and regards
Mike
support@str8creative.co
Thursday, October 22, 2020
Domain Authority 50 for your website - Guaranteed Service
cent
for only 150 usd, you`ll have DA50 for your website, guaranteed
Order it today:
http://www.str8-creative.co/product/moz-da-seo-plan/
thanks
Alex Peters
Saturday, September 26, 2020
Domain Authority 50 for your website - Guaranteed Service
cent
for only 150 usd, you`ll have DA50 for your website, guaranteed
Order it today:
http://www.str8-creative.co/product/moz-da-seo-plan/
thanks
Alex Peters
Tuesday, September 22, 2020
Curved Region Rendering
Around a month ago I had an idea in my head: a voronoi grid modified to have rounded cells that change in size. I made an attempt here for single cells changing size. The next step was to merge cells together, as I had done on this project. I decided that the way to demo this would be to simulate some kind of belief/cultural systems that spread over time across a map. I tried this here.
It didn't go well.
What happened? I think the problem was that I had three unknown elements in this project:
- Simulation with the simplest rendering code I could get away with. Figure out what simulation rules are interesting and cool.
- Rendering isolines on a triangle mesh.
- Rendering curved isolines on a triangle mesh, using Bezier curves.
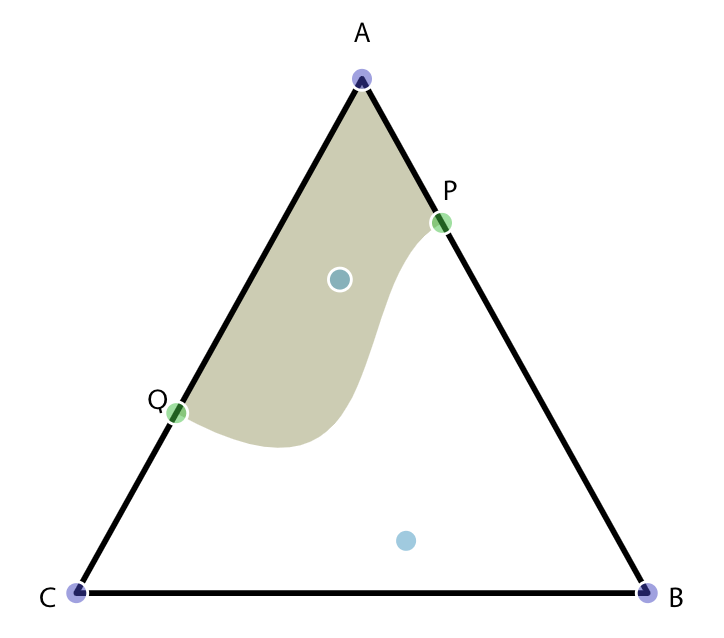
In trying to figure out all three at once, I didn't do a good job on them. I should have instead focused on one at a time. I ended up succeeding with #2 when I learned about and implemented the Meandering Triangles algorithm, and also built a little interactive visualization that helped me understand how the algorithm works. I failed with #1, having tried several algorithms but not finding one that I liked. I realized towards the end of the week that #1 was a red herring; I didn't need a simulation at all, as I really just wanted curved regions. I also failed at #3, having tried some experiments but never finding what I wanted, and also rejecting Chaikin Curves for reasons I can't remember. Since I really wanted the curved variable sized regions, I should have spent more time on #3 and less on #1. I ran out of time on this project so I'll leave #1 and #3 for another day.
You can see the animation I ended up with.
What do I mean "I ran out of time"? That's the next blog post!
Monday, September 21, 2020
Roll West, Young Man...
"Roll and write" is an emerging style of game that seeks to reduce production costs by eschewing cards, tiles and tokens in favor of players simply marking changes to the game state on a piece of paper with a pencil or pen. This allows these games to be sold at a much lower price point, which can only be an asset in the increasingly crowded board game market.
Actually, roll and write games have been around for many years, with Yahtzee usually pointed to as the first commercial example. But the genre has exploded in recent years, either as a way for game publishers to increase their visibility in stores by putting out simplified versions of games like Settlers of Catan or Patchwork, but just as often with off-the-wall ideas that might not support a $60 board game.
We picked up Rolled West on a whim, having not played any roll and write games (other than Yahtzee), and also having not played Gold West, the full board game it's based on,. So we should be able to judge the game on its own merits without comparison to its parent game or other games in the same genre.
Each player is given a dry-erase board showing what initially looks like a dizzying array of icons. But once you play a few times it's pretty straightforward. The icons represent banked resources, boom town buildings, shipment routes, and mining contracts and claims. On his or her turn, the acting player rolls 4 dice showing symbols that equate to copper, silver, gold, and wood. The player chooses one of these to represent the terrain for the turn, and the other three are resources that can either be spent or banked for use on a future turn.
Players spend combinations of resources on the aforementioned buildings, routes, contracts and claim, with an eye towards maximizing their points at the end of the game. There are a lot of options, so clever players will quickly identify a particular strategy, such as staking claims and building mining camps, developing shipping routes, or saving up resources to buy expensive but lucrative contracts, and then staying with that strategy over the course of the game's six turns. Trying to do a little of everything, or changing strategies mid-game, can be disastrous, as the points tend to rack up the farther along you go on a single track, such as staking claims in the woods or developing a shipping line for silver ore.
Boom town buildings confer bonus points based on the other things you've developed in the game, which can be tricky since you don't want to invest in a particular building before you've figured out what your strategy is. At the same time, as soon as one player buys a building it is no longer available to the other players (the corresponding icon is crossed off on their board), so you don't want to wait too long either.
Players also have the option to bank one resource each turn for future use. Banking resources is really the only way to save up for high value contracts that generally require four or five resources but are worth a lot of points at the end of the game, Additionally, in between each of a player's turns they can bank one of the resources rolled by another player. This doesn't prevent the other player from using it, it just allows you to use it also. This is one of the more interesting decision points in the game, since it can only be done once between each turn -- you're always running the risk of banking a resource, only to have someone else roll a more useful one before your turn comes around again.
As you can see, there is a lot going on here, especially for a game that consists of four dice and what amounts to a 4x6 card for each player. My only complaint about the game is that the iconography on the player cards can be a bit difficult to remember, causing frequent referral to the rules to answer "what does this mean again?" questions. It might have been better to make the player boards larger and include gameplay reminders and tips.
Rating: 4 (out of 5) It's got a huge amount of depth for such a simple game, and yet it can still be played in 30 minutes or so.
- Rolled West on BoardGameGeek
- Weirdly, there is no mention of this game on the publisher's website
Wednesday, September 16, 2020
1500 google maps citations cheap
http://www.str8-creative.io/product/1500-gmaps-citations/
regards,
Str8 Creative
Saturday, September 12, 2020
People Behind The Meeples - Episode 242: Steven Ridings

Welcome to People Behind the Meeples, a series of interviews with indie game designers. Here you'll find out more than you ever wanted to know about the people who make the best games that you may or may not have heard of before. If you'd like to be featured, head over to http://gjjgames.blogspot.com/p/game-designer-interview-questionnaire.html and fill out the questionnaire! You can find all the interviews here: People Behind the Meeples. Support me on Patreon!
| Name: | Steven Ridings |
|---|---|
| Email: | cretaceousboardgame@gmail.com |
| Location: | Pennsylvania - United States |
| Day Job: | 3D Modeler - Environmental Artist |
| Designing: | One to two years. |
| Webpage: | Cretaceous |
| Facebook: | Cretaceous Board Game |
| Twitter: | @cretaceous_game |
| Instagram: | @cretaceousboardgame/ |
| Find my games at: | Cretaceous: A Dinosaur Hunting Adventure is on Kickstarter in August 2020, Gamecrafter after the campaign |
Steven Ridings
Interviewed on: 7/17/2020
This week's interview is with Steven Ridings, the designer of Cretaceous: A Dinosaur Hunting Adventure, on Kickstarter right now! Read on to learn more about Steven and his projects.
Some Basics
Tell me a bit about yourself.
How long have you been designing tabletop games?
One to two years.
Why did you start designing tabletop games?
I wanted to create something people could have fun with. I am a 3D modeler professionally and I got into it in order to make video games to give people fun, emotional experiences. However I found myself in the government contracting side of the field and while I enjoy what I do, it doesn't scratch that itch to provide people with a fun experience and since I get that from board games it seemed like a great hobby to get into the design side of things.
What game or games are you currently working on?
Cretaceous: A Dinosaur Hunting Adventure
Have you designed any games that have been published?
Not yet!
What is your day job?
3D Modeler - Environmental Artist
Your Gaming Tastes
My readers would like to know more about you as a gamer.
Where do you prefer to play games?
At home or at a friends house. I definitely feel the most comfortable to be loud and just relax.
Who do you normally game with?
Well I have two real groups. One I grew up with in Winchester VA and try to play anytime I swing through town. Another my wife and I met online playing video games and dungeons and dragons.
If you were to invite a few friends together for game night tonight, what games would you play?
I'd say my top two would be Clank! and Evolution. Some runner ups would have to be Dinosaur Island, Betrayal at House on the Hill, and Arkham Horror.
And what snacks would you eat?
Red Baron mini frozen pizzas have kind of become a signature food over here when friends visit. Maybe add some cheetos or chips too.
Do you like to have music playing while you play games? If so, what kind?
We don't, but a buddy of mine always had it when we played Magic and it was cool. Maybe it's something we should start.
What's your favorite FLGS?
I have two since we travel a lot back and forth to VA normally. In Winchester VA there is Kung Fu Comics. It's run by a long time friend and has everything from MTG, board games, and miniatures. In Pennsylvania I would have to say New Dimension Comics. They have a HUGE store at the waterfront and I met my D&D group there.
What is your current favorite game? Least favorite that you still enjoy? Worst game you ever played?
Current favorite would be Dinosaur Island. Making Cretaceous really got me more into a dino mood. Least that I still enjoy would be Joking Hazard as you seem to get the same cards pretty fast so if you play it a lot it starts to get a bit repetitive. I feel a bit bad putting a worst but I would have to say Keys to the Castle. I saw it on sale and I should have known better with no gameplay art on the box but we gave it a try. It's been gathering dust since.
What is your favorite game mechanic? How about your least favorite?
Tile placement and map building are my favorite. I want at the end of the game to look at something and see something that wasn't there when we started. That's one of the main reasons Cretaceous makes the map as you go and spawns dinosaurs during the game, so the map comes to life as you play. My least favorite would be games that put too much power in the cards to draw like Cards Against Humanity or most card only games that have a random draw. It seems that based on what you draw you win or lose and sometimes you know you have lost early based on a "bad hand" and you get to wait for the next round without much of a chance to change that.
What's your favorite game that you just can't ever seem to get to the table?
Arkham Horror. Since there are so many parts to it, it seems a bit overwhelming to new players.
What styles of games do you play?
I like to play Board Games, Card Games, Miniatures Games, RPG Games, Video Games
Do you design different styles of games than what you play?
I like to design Board Games
OK, here's a pretty polarizing game. Do you like and play Cards Against Humanity?
No
You as a Designer
OK, now the bit that sets you apart from the typical gamer. Let's find out about you as a game designer.
When you design games, do you come up with a theme first and build the mechanics around that? Or do you come up with mechanics and then add a theme? Or something else?
I definitely do the theme first. I want to pull a certain feeling out of people and I can get that from the theme. For Cretaceous I wanted the feeling of going through a jungle or forest not knowing what dinosaurs or hazards there would be. It started as a game where you were trying to escape an island and avoid the dinosaurs but slowly the mechanics changed to something far more fun but still gave that same feeling.
Have you ever entered or won a game design competition?
No, I have not entered any. I've only really been focusing on Cretaceous and I didn't want to submit it without all the artwork done. Maybe now that it is at a place I am happy with I can submit it to a few.
Do you have a current favorite game designer or idol?
Definitely Dominic Crapuchettes. The first Evolution really pulled me into the modern board game world and I was so into that game I took it every time I visited friends. They now request and make sure I bring it. And the story of how he came to design board games is amazing as well.
Where or when or how do you get your inspiration or come up with your best ideas?
I'd say my best ideas would come from when I can just sit for 30-60 minute sessions by myself and just write down any ideas for the game. I wont keep most of them, but being able to compare the pool of thoughts easily lets me narrow down to the best ways to accomplish what I want.
How do you go about playtesting your games?
Annoying my wife with countless index card prototypes! But in all seriousness for Cretaceous I remade it a few times with her until I found something I thought was a good base. Then I took it to VA when we visited to get more feedback. After some Game Crafter prototypes to get a feel of costs and components I took it to Tabletop Simulator and reached out to people online. I was planning on more local game store tests instead but with 2020 being what it is, that moved online.
Do you like to work alone or as part of a team? Co-designers, artists, etc.?
I'd like to work with others in the future. Specifically an artist as I believe my skills are limited. Although through all the playtesters I got a lot of great ideas that improved the game, so I can't really say I made it alone.
What do you feel is your biggest challenge as a game designer?
That this is my first game and nobody knows whether to invest in anything I make.
If you could design a game within any IP, what would it be?
The cast of Critical Role for a board game based on one of their two campaigns. They have such rich lore and worlds built that they could go into any media!
What do you wish someone had told you a long time ago about designing games?
I didn't know the Game Crafter was a thing until a little over a year ago. I just had ideas in my head but didn't know how to get it on a real product easily.
What advice would you like to share about designing games?
Make sure to playtest even a really early draft of your game. Even if it is just on index cards. No matter how well you think it will work out, just playing it once will expose things you need to change. Once you finally don't see any major issues, then grab a few more testers and maybe make a better prototype.
Would you like to tell my readers what games you're working on and how far along they are?
This is what I have currently crowdfunding: Cretaceous: A Dinosaur Hunting Adventure
Games that are in the early stages of development and beta testing are: An interesting crafting and creation game is looking pretty fun
Are you a member of any Facebook or other design groups? (Game Maker's Lab, Card and Board Game Developers Guild, etc.)
TGC Designer Discussion
And the oddly personal, but harmless stuff…
OK, enough of the game stuff, let's find out what really makes you tick! These are the questions that I'm sure are on everyone's minds!
Star Trek or Star Wars? Coke or Pepsi? VHS or Betamax?
Star Wars / Pepsi / VHS
What hobbies do you have besides tabletop games?
Retro Video game Collecting and Fishing
What is something you learned in the last week?
Taco Bell has a Grilled Cheese Burrito
Favorite type of music? Books? Movies?
Comedy / Parody Music Fantasy Books 3D Animation Movies like Pixar or Dreamworks
What was the last book you read?
Does the Baldur's Gate campaign book count?
Do you play any musical instruments?
Nope! But if I could, I would choose Violin.
Tell us something about yourself that you think might surprise people.
I don't really like horror movies or books, but for some reason I really like the game Dead by Daylight.
Tell us about something crazy that you once did.
I put Cheetos on a pizza. I used the Joey Tribbiani approach. Pizza? Good. Cheetos? Good. What is there not to like? (It didn't go well)
Biggest accident that turned out awesome?
I didn't know those could turn out well. I'll keep a lookout.
Who is your idol?
Weird Al. He did something he loved that did not fit any of the norms of the time. Accordion parody music wasn't really "in". But he brought so much joy and laughter to the world because he was just himself.
What would you do if you had a time machine?
I think I would be worried about screwing something up in the present. So I guess drop it in the ocean.
Are you an extrovert or introvert?
Introvert. Extremely so.
If you could be any superhero, which one would you be?
Superman. I don't really like DC but the guy has it all. It's like getting to choose multiple choices on this one.
Have any pets?
2 Cats - Nami and Jinx 2 Rabbits - Kisa and Roshi
When the next asteroid hits Earth, causing the Yellowstone caldera to explode, California to fall into the ocean, the sea levels to rise, and the next ice age to set in, what current games or other pastimes do you think (or hope) will survive into the next era of human civilization? What do you hope is underneath that asteroid to be wiped out of the human consciousness forever?
Survive - A thumb drive that some Pirate has filled with all the ROMS of classic video games from NES, SNES, and 64. I bet they would fit. Destroyed - Durian Fruits
If you'd like to send a shout out to anyone, anyone at all, here's your chance (I can't guarantee they'll read this though):
I'd like to thank my wife Kathleen the most. She helped push me to thinking my games would be worth making and not to doubt myself so much. It's really hard to get over the self doubt sometimes.
Thanks for answering all my crazy questions!
Thank you for reading this People Behind the Meeples indie game designer interview! You can find all the interviews here: People Behind the Meeples and if you'd like to be featured yourself, you can fill out the questionnaire here: http://gjjgames.blogspot.com/p/game-designer-interview-questionnaire.html
Did you like this interview? Please show your support: Support me on Patreon! Or click the heart at Board Game Links
 , like GJJ Games on Facebook
, like GJJ Games on Facebook  , or follow on Twitter
, or follow on Twitter  . And be sure to check out my games on Tabletop Generation.
. And be sure to check out my games on Tabletop Generation.Cha'alt Play Report
I took time off from virtual gaming, like the entire lockdown. That's 5 months.
Partly, this was because I was finishing up Cha'alt: Fuchsia Malaise. The rest was due to my being mentally, emotionally, and physically exhausted... I've been running my very own in-home daycare (ages 3-9).
Flush with excitement from updating my transparent aluminum (so light weight and durable) O5R house-rules / hack of D&D known as Crimson Dragon Slayer (arcade-mode, bitches!), I ran a 90-minute one-shot of Cha'alt on Roll20.
A couple people dropped out because my way of running 5e isn't RAW enough for them, but we still had a decent party of 4 1/2 players (one guy was late and didn't quite get the hang of the chat until the very end).
The reason I like fast and dirty character creation is because I want to get playing. And if you get killed, go ahead and think of a new guy and jump back in the next scene. Everyone's time is valuable. If I know you're playing a chaotic elf fighter named Gera'ald with a penchant for tentacle cow-tipping, that basically tells me all the mechanical and flavor junk I need to know as the GM.
The PCs had been wandering for a few hours before coming to a well-known landmark in the desert wasteland known as S'kbah. The adventurers stood on the edge of a sarla'ak pit, it's gaping mouth wide and sun-burnt tentacles writhing hungrily.
20' above floated a hover-skiff containing a prisoner, two Federation guards, and a man wearing all-black. It appeared that the prisoner was going to be executed very soon.
After some chit-chat with the Federation people, a PC (pixie-fairy thief) flew up and helped the prisoner get his hands free. Fighting soon commenced. Weirdly, two of the players chose clerics as characters but only a single healing spell was cast the entire game. Hand-crossbows versus blasters, the PCs were taking heavy losses. Feeling cocky, the man in black ignited a purple laser-sword and jumped down to engage the party's only fighter - a reptilian named Drak'thiss.
I missed every single attack with the man in black, so he eventually fell after the PCs flanking him both rolled a critical hit. In the meantime, the prisoner had run off.
The survivors looted the bodies and started walking as night approached. Replacement characters met up with the party and shortly after discovered the prisoner crawling on the sand, dehydrated and near death.
One PC helped him up and gave him water. Everyone listened to the prisoner's promise of wealth and power if they kept him alive long enough to get off-world. He mentioned the infamous black pyramid...
Two seconds later, another PC attempted to brain him with a mace. He missed and the other PCs brushed it off with uncomfortable laughter, somehow unable to see the giant red flag being waved in front of their faces. Next round, that same PC shot him point-blank in the head.
A couple of the other PCs complained about their comrade's rash action, but they didn't take up arms against him. And then we were out of time.
While I'm running the game, I try not to judge. I may slightly nudge adventurers in a certain direction from time to time, but ultimately it's their choice.
Now, that the game is over... well, let's just say mistakes were made. Nothing was set in stone. The scenario could have gone in one of a dozen different directions. Next time I run the same scenario, it'll go a different way. Always does.
If you choose to GM your own introduction to Cha'alt, feel free to use that (completely and utterly original start-point), and ask me for further information on the NPCs, possible future plans, etc.
VS
p.s. I still have 40-something luxury Cha'alt hardcovers left. Want one before they're gone? Here ya go, hoss!
Thursday, September 10, 2020
Domain Authority 50 for your website - Guaranteed Service
cent
for only 150 usd, you`ll have DA50 for your website, guaranteed
Order it today:
http://www.str8-creative.co/product/moz-da-seo-plan/
thanks
Alex Peters
Friday, September 4, 2020
ASOIAF: Rodrik Cassel 40Pt Army
 |
| Let's get down to business. |
Winter has come. While there are some people out there that prefer to go maneuver-heavy with Robb or face-smashy with Greatjon Umber, I like going Rodrik Cassel. The reason why is because his tactics cards are absolutely bonkers and making units Vulnerable just makes a smashy faction even smashier.
First, let's take a look at Rodrik Cassel and see what he offers to our army:
 |
| A true soldier. |
As you can see, Rodrik is a soldier who has an Order to make the opponent's unit Vulnerable after Attack dice are rolled. The timing for this is exceptionally important because it's what Sworn Sword Captains have as well and it's considered one of the best 1-point attachments in the game. Vulnerable is huge for someone like Rodrik because it unlocks his Tactics cards and skyrockets the damage potential of all your units. Having Vulnerable on something after you charge it would mean you re-roll all hits and your opponent has to essentially re-roll all their successful saves. It pretty much means the Stark army will obliterate units that have low saves or punch through tougher targets that can normally deflect their blows. Peeling ranks off enemy units will also keep your units around longer as the enemies' damage potential will decrease.
Let's take a look at Rodrik's tactics cards:
 |
| All that martial goodness! |
Martial Superiority is one of the best defensive tactics cards in the game. It triggers off when the enemy unit attacks and that dice rolls less dice AND loses all abilities until the end of the turn. Now, it isn't as powerful as some of the silences we've been before where it lasts until the end of the round, but this card doesn't need any conditionals like expending condition tokens or anything else. You cast it, boom, and most of the opponent's plans are foiled. This card is amazing at stopping something like Gregor + Flayed Men from rolling a unit while you set up for a counter-attack. To make things even more interesting, if you're going after Rodrik's unit, good luck. Having Weakened on top of this card pretty much means Rodrik's units going to stay around. Combat Prowess is a great follow-up card when used with Rodrik's unit or with any unit under the influence of Vulnerable. What if your opponent rolls poorly and you don't need to spend the Vulnerable token? Guess like he's being silenced and unable to respond with any defensive tactics cards. It's really fierce when used on the charge as there are fewer things in the game that interacts with that timing window than when a friendly unit attacks. Lastly, we have Press the Advantage. This is another one of those cards that trigger off the attack so you can't use a Sworn Sword Captain's Orders and then play this card because it escapes the window. What this card does is kick your opponents when they're already down because of the Critical Blows on an already Vulnerable target. That's why I have taken a unit of Tully Sworn Shields with Rodrik because it makes them one of the tankiest units in the game while giving them the opportunity to do bigger damage than their stats suggest.
Here's the list:
Faction: House Stark
Commander: Rodrik Cassel – Master–at–Arms
Points: 40 (4 Neutral)
Combat Units:
• Stark Sworn Swords (5)
with Sworn Sword Captain (1)
• House Umber Greataxes (7)
with Robb Stark – The Young Wolf (3)
• Grey Wind (0)
• House Tully Sworn Shields (7)
with Rodrik Cassel – Master–at–Arms (0)
• Stark Outriders (7)
with Brynden Tully – Vanguard Infiltrator (3)
Non-Combat Units:
• Sansa Stark – Little Bird (3)
• Petyr Baelish – Littlefinger (4)
Made with ASOIAFBuilder.com
Let me try and explain some of these choices super quick. The Stark Sword Swords are simply one of the best offensive units in the game for the cost. With Stark Fury and 8 dice on a 5-point unit and the ability to make someone Vulnerable, the damage potential for this unit is huge. Great Axes deal a huge amount of damage and can definitely wreck heavy cavalry if they're already engaged with them. Robb Stark as an attachment makes them regular infantry speed and gives you the ability to launch yourself out there on a Maneuver trigger on the tactics board. This makes two units that can do it in the army and that will surprise your opponents a lot! The fact that Robb (and Bran) come with their Dire Wolves is one of the best things about Starks. These free wolves not only come with great abilities, but they're a free activation and deploy to be used in battle. Grey Wind is especially good because he is able to apply Vulnerable onto a unit if already used, or apply it beforehand so it can be consumed using Rodrik's own ability or tactics cards.
I already explained a little bit about the Tully Sworn Shields above, but with Rodrik's tactics cards, this unit becomes a very jack-of-all-trades unit. It's already super defensive with Shield Wall and 3+ save, but cards like Martial Superiority just takes it over the edge. While the defensive stats normally lower damage expectations, Press the Advantage and Vulnerable tokens in general greatly increases its damage potential. As for Stark Outriders, I think they're a great, solid unit at 7 points. With Brynden Tully however, they can be one of the most annoying units in the game thanks for their great flanking ability and healing on retreat. A lot of the Stark tactics cards play incredibly well with Outriders as well thanks to their unpredictable damage potential. Just remember that with 7-point units, you can also decide to trade out the Sworn Shields for a unit of Berserkers if you want some more face-smash.
 |
| "And yet you betrayed me.." |
As for NCUs, I really like Sansa Stark with Rodrik because of her ability to recycle or tutor for exactly what is needed right then and there. While we all try and anticipate everything that is going to happen in a game, Sansa offers us extra insurance that if an opponent rolls a 6 for a long ass charge you didn't anticipate and is rolling in with crazy Tactics cards in support, you always have a way to Martial Superiority him into the ground. For my next NCU, believe it or not, I think Littlefinger is a solid choice for the Starks. It's just comical that I'm taking both Sansa and Littlefinger in the same list, but his ability to claim Combat/Maneuver that unlocks the secondary capabilities for your Stark tactics cards while still reaping the benefit of other unclaimed zones is amazing.
Try out the list and let me know how you fair!
Monday, August 31, 2020
CEH: 10 Hacking Tools For Hackers
There are a lot of hacking tools available over the internet but mostly we need some of them. In this blog you'll learn about hacking tools which are typically used in the world of hacking by penetration testers.
SmartWhois
SmartWhois is an information-gathering program that allows you to find all available information about an IP address, hostname, or domain, including country, state or province, city, name of the network provider, administrator, and technical support contact information. SmartWhois is a graphical version of the basic Whois program.SocksChain
SocksChain is a tool that gives a hacker the ability to attack through a chain of proxy servers. The main purpose of doing this is to hide the hacker's real IP address and therefore minimize the chance of detection. When a hacker works through several proxy servers in series, it's much harder to locate the hacker. Tracking the attacker's IP address through the logs of several proxy servers is complex and tedious work. If one of the proxy servers' log files is lost or incomplete, the chain is broken, and the hacker's IP address remains anonymous.NeoTrace, VisualRoute, and VisualLookout
NeoTrace, VisualRoute, and VisualLookout are all packet-tracking tools with a GUI or visual interface. They plot the path the packets travel on a map and can visually identify the locations of routers and other internet working devices. These tools operate similarly to traceroute and perform the same information gathering; however, they provide a visual representation of the results.Visualware's eMailTrackerPro
Visualware's eMailTrackerPro ( www.emailtrackerpro.com/ ) and MailTracking ( http://mailtracking.com/ ) are tools that allow an ethical hacker to track email messages. When you use these tools to send an email, forward an email, reply to an email, or modify an email, the resulting actions and tracks of the original email are logged. The sender is notified of all actions performed on the tracked email by an automatically generated email.IPEye
IPEye is a TCP port scanner that can do SYN, FIN, Null, and XMAS scans. It's a command line tool.IPEye probes the ports on a target system and responds with closed, reject, drop, or open. Closed means there is a computer on the other end, but it doesn't listen at the port. Reject means a firewall is rejecting the connection to the port (sending a reset back). Drop means a firewall is dropping everything to the port, or there is no computer on the other end. Open means some kind of service is listening at the port. These responses help a hacker identify what type of system is responding.
IPSecScan
IPSecScan is a tool that can scan either a single IP address or a range of addresses looking for systems that are IPSec enabled that means the system has IPSec enabled while disabled means that it either has IPSec disabled, the compatibility issue or the configuration issue that not reveal to you that it has IPSec enabled. Indeterminable means that the scanner isn't sure if IPSec is enabled or disabled.Icmpenum
Icmpenum uses not only ICMP Echo packets to probe networks, but also ICMP Timestamp and ICMP Information packets. Furthermore, it supports spoofing and sniffing for reply packets. Icmpenum is great for scanning networks when the firewall blocks ICMP Echo packets but fails to block Timestamp or Information packets.SNMP Scanner
SNMP Scanner allows you to scan a range or list of hosts performing ping, DNS, and Simple Network Management Protocol (SNMP) queries. This tool helps you to find out the current information about the device of SNMP nodes in the given network.hping2 tool
The hping2 tool is notable because it contains a host of other features besides OS fingerprinting such as TCP, User Datagram Protocol (UDP), ICMP, and raw-IP ping protocols, traceroute mode, and the ability to send files between the source and target system.THC-Scan, PhoneSweep, and TeleSweep
THC-Scan, PhoneSweep, and TeleSweep are tools that identify phone numbers and can dial a target to make a connection with a computer modem. These tools generally work by using a predetermined list of common usernames and passwords in an attempt to gain access to the system. Most remote-access dial-in connections aren't secured with a password or use very rudimentary security.More articles- Black Hat Hacker Tools
- Hacker Tools Mac
- Hacker Search Tools
- Install Pentest Tools Ubuntu
- New Hack Tools
- Pentest Tools Online
- Free Pentest Tools For Windows
- How To Install Pentest Tools In Ubuntu
- Android Hack Tools Github
- Hack Tools For Ubuntu
- Beginner Hacker Tools
- Hack App
- Hacking Tools Free Download
- Hacking Tools Mac
- Hacking Apps
- Hacking Tools For Windows Free Download
- Tools For Hacker
- Blackhat Hacker Tools
- Hack Tools
- Hacker Security Tools
- Hacker Hardware Tools
- Hacker Tools Linux
- Hacker Hardware Tools
- Beginner Hacker Tools
- Pentest Tools Tcp Port Scanner
- How To Hack
- Hacking Tools For Mac
- Physical Pentest Tools
- Hacking Apps
- Hacker Tools
- Hacking Tools 2019
- Pentest Tools Windows
- Pentest Tools Website Vulnerability
- Hacking App
- Ethical Hacker Tools
- Pentest Automation Tools
- Install Pentest Tools Ubuntu
- Pentest Tools For Ubuntu
- Hacker Tools For Ios
- What Is Hacking Tools
- Hacking Tools Free Download
- Hack Tools
- Beginner Hacker Tools
- Hacking Tools 2020
- Hack Tools For Pc
- Tools Used For Hacking
- Pentest Tools Linux
- Ethical Hacker Tools
- Hak5 Tools
- Pentest Tools For Android
- New Hack Tools
- Hack Tools For Mac
- Best Hacking Tools 2019
- Hacking App
- Pentest Tools For Windows
- Pentest Recon Tools
- Hack Tools
- Pentest Tools Kali Linux
- What Is Hacking Tools
- Pentest Tools Linux
- Hackers Toolbox
- Hack App
- Pentest Tools Linux
- Tools For Hacker
- Top Pentest Tools
- Hacker Tools For Windows
- Pentest Recon Tools
- Pentest Tools Apk
- Best Hacking Tools 2020
- Hacker Tools Apk Download
- Game Hacking
- Hacker
- Best Hacking Tools 2020
- Hacker Tools Github
- Bluetooth Hacking Tools Kali
- Pentest Tools Review
- Nsa Hack Tools Download
- Hacking Tools For Beginners
- How To Make Hacking Tools
Sunday, August 30, 2020
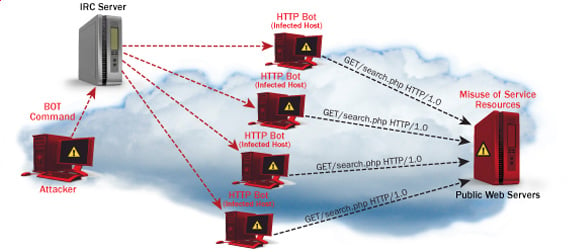
DOS (Denial Of Service) Attack Tutorial Ping Of Death ;DDOS
What is DoS Attack?
DOS is an attack used to deny legitimate users access to a resource such as accessing a website, network, emails, etc. or making it extremely slow. DoS is the acronym for Denial of Service. This type of attack is usually implemented by hitting the target resource such as a web server with too many requests at the same time. This results in the server failing to respond to all the requests. The effect of this can either be crashing the servers or slowing them down.
Cutting off some business from the internet can lead to significant loss of business or money. The internet and computer networks power a lot of businesses. Some organizations such as payment gateways, e-commerce sites entirely depend on the internet to do business.
In this tutorial, we will introduce you to what denial of service attack is, how it is performed and how you can protect against such attacks.
Topics covered in this tutorial
- Types of Dos Attacks
- How DoS attacks work
- DoS attack tools
- DoS Protection: Prevent an attack
- Hacking Activity: Ping of Death
- Hacking Activity: Launch a DOS attack
Types of Dos Attacks
There are two types of Dos attacks namely;
- DoS– this type of attack is performed by a single host
- Distributed DoS– this type of attack is performed by a number of compromised machines that all target the same victim. It floods the network with data packets.
How DoS attacks work
Let's look at how DoS attacks are performed and the techniques used. We will look at five common types of attacks.
Ping of Death
The ping command is usually used to test the availability of a network resource. It works by sending small data packets to the network resource. The ping of death takes advantage of this and sends data packets above the maximum limit (65,536 bytes) that TCP/IP allows. TCP/IP fragmentation breaks the packets into small chunks that are sent to the server. Since the sent data packages are larger than what the server can handle, the server can freeze, reboot, or crash.
Smurf
This type of attack uses large amounts of Internet Control Message Protocol (ICMP) ping traffic target at an Internet Broadcast Address. The reply IP address is spoofed to that of the intended victim. All the replies are sent to the victim instead of the IP used for the pings. Since a single Internet Broadcast Address can support a maximum of 255 hosts, a smurf attack amplifies a single ping 255 times. The effect of this is slowing down the network to a point where it is impossible to use it.
Buffer overflow
A buffer is a temporal storage location in RAM that is used to hold data so that the CPU can manipulate it before writing it back to the disc. Buffers have a size limit. This type of attack loads the buffer with more data that it can hold. This causes the buffer to overflow and corrupt the data it holds. An example of a buffer overflow is sending emails with file names that have 256 characters.
Teardrop
This type of attack uses larger data packets. TCP/IP breaks them into fragments that are assembled on the receiving host. The attacker manipulates the packets as they are sent so that they overlap each other. This can cause the intended victim to crash as it tries to re-assemble the packets.
SYN attack
SYN is a short form for Synchronize. This type of attack takes advantage of the three-way handshake to establish communication using TCP. SYN attack works by flooding the victim with incomplete SYN messages. This causes the victim machine to allocate memory resources that are never used and deny access to legitimate users.
DoS attack tools
The following are some of the tools that can be used to perform DoS attacks.
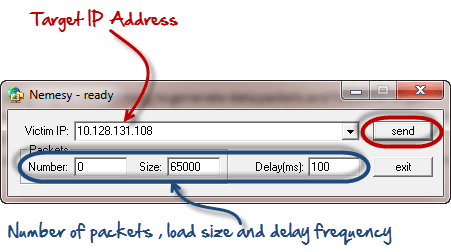
- Nemesy– this tool can be used to generate random packets. It works on windows. This tool can be downloaded from http://packetstormsecurity.com/files/25599/nemesy13.zip.html . Due to the nature of the program, if you have an antivirus, it will most likely be detected as a virus.
- Land and LaTierra– this tool can be used for IP spoofing and opening TCP connections
- Blast– this tool can be downloaded from http://www.opencomm.co.uk/products/blast/features.php
- Panther- this tool can be used to flood a victim's network with UDP packets.
- Botnets– these are multitudes of compromised computers on the Internet that can be used to perform a distributed denial of service attack.
DoS Protection: Prevent an attack
An organization can adopt the following policy to protect itself against Denial of Service attacks.
- Attacks such as SYN flooding take advantage of bugs in the operating system. Installing security patches can help reduce the chances of such attacks.
- Intrusion detection systems can also be used to identify and even stop illegal activities
- Firewalls can be used to stop simple DoS attacks by blocking all traffic coming from an attacker by identifying his IP.
- Routers can be configured via the Access Control List to limit access to the network and drop suspected illegal traffic.
Hacking Activity: Ping of Death
We will assume you are using Windows for this exercise. We will also assume that you have at least two computers that are on the same network. DOS attacks are illegal on networks that you are not authorized to do so. This is why you will need to setup your own network for this exercise.
Open the command prompt on the target computer
Enter the command ipconfig. You will get results similar to the ones shown below
For this example, we are using Mobile Broadband connection details. Take note of the IP address. Note: for this example to be more effective, and you must use a LAN network.
Switch to the computer that you want to use for the attack and open the command prompt
We will ping our victim computer with infinite data packets of 65500
Enter the following command
ping 10.128.131.108 –t |65500
HERE,
- "ping" sends the data packets to the victim
- "10.128.131.108" is the IP address of the victim
- "-t" means the data packets should be sent until the program is stopped
- "-l" specifies the data load to be sent to the victim
You will get results similar to the ones shown below
Flooding the target computer with data packets doesn't have much effect on the victim. In order for the attack to be more effective, you should attack the target computer with pings from more than one computer.
The above attack can be used to attacker routers, web servers etc.
If you want to see the effects of the attack on the target computer, you can open the task manager and view the network activities.
- Right click on the taskbar
- Select start task manager
- Click on the network tab
- You will get results similar to the following
If the attack is successful, you should be able to see increased network activities.
Hacking Activity: Launch a DOS attack
In this practical scenario, we are going to use Nemesy to generate data packets and flood the target computer, router or server.
As stated above, Nemesy will be detected as an illegal program by your anti-virus. You will have to disable the anti-virus for this exercise.
- Download Nemesy from http://packetstormsecurity.com/files/25599/nemesy13.zip.html
- Unzip it and run the program Nemesy.exe
- You will get the following interface
Enter the target IP address, in this example; we have used the target IP we used in the above example.
HERE,
- 0 as the number of packets means infinity. You can set it to the desired number if you do not want to send, infinity data packets
- The size field specifies the data bytes to be sent and the delay specifies the time interval in milliseconds.
Click on send button
You should be able to see the following results
The title bar will show you the number of packets sent
Click on halt button to stop the program from sending data packets.
You can monitor the task manager of the target computer to see the network activities.
Summary
- A denial of service attack's intent is to deny legitimate users access to a resource such as a network, server etc.
- There are two types of attacks, denial of service and distributed denial of service.
- A denial of service attack can be carried out using SYN Flooding, Ping of Death, Teardrop, Smurf or buffer overflow
- Security patches for operating systems, router configuration, firewalls and intrusion detection systems can be used to protect against denial of service attacks.
Related articles
- Pentest Tools Subdomain
- Hacker Techniques Tools And Incident Handling
- Kik Hack Tools
- Hacking Tools Github
- Pentest Tools Nmap
- Hacker Tools Windows
- Hacker Tools 2020
- Pentest Tools Windows
- Hackrf Tools
- Pentest Tools Website
- Hacking Tools And Software
- Hacker Hardware Tools
- Hackrf Tools
- New Hack Tools
- Pentest Tools Windows
- Hack Rom Tools
- Pentest Tools For Mac
- Pentest Tools Online
- Hacker Tools Mac
- Pentest Tools Free
- Hacker Tools Mac
- Black Hat Hacker Tools
- Easy Hack Tools
- Hacker Techniques Tools And Incident Handling
- Hack Tools 2019
- Hacker Tools Apk
- Kik Hack Tools
- Pentest Tools For Mac
- Hacking Tools Hardware
- Computer Hacker
- Pentest Tools Windows
- Best Pentesting Tools 2018
- Hak5 Tools
- Hackrf Tools
- Best Hacking Tools 2019
- Wifi Hacker Tools For Windows
- Pentest Tools Github
- Pentest Tools Subdomain
- Hacker Security Tools
- Hacker Tools Hardware
- Github Hacking Tools
- Hacking Tools For Beginners
- Hacker Tools Online
- Pentest Tools Windows
- Game Hacking
- Hacker Security Tools
- Hacker Tools Windows
- Pentest Tools For Mac
- Hack Tools Github
- Hacking Tools For Kali Linux
- Computer Hacker
- Hacking Tools For Windows
- Hacker Search Tools
- What Are Hacking Tools
- Hacking Tools Pc
- Hacking Tools Windows
- Pentest Tools
- Top Pentest Tools
- Hacking Tools Mac
- Growth Hacker Tools
- Android Hack Tools Github
- Hacking Tools Software
- Hacking Tools Download
- Hacking App
- Hacker Tools For Mac
- Hacking App
- Kik Hack Tools
- Hacker Tools For Pc
- Tools Used For Hacking
- Hacker Tools Mac
- Hack Tools For Games
- Pentest Recon Tools
- Hacking Tools Kit
- Hacking Tools For Pc
- Hacker Tools For Pc
- Best Pentesting Tools 2018
- Hacker Tools 2020
- Underground Hacker Sites
- World No 1 Hacker Software
- Hacker Tool Kit
- Hacker Tools List
- Hacking Tools 2019
- Github Hacking Tools
- Hacker Tools Windows
- Computer Hacker
- Nsa Hack Tools
- Hacking Tools Online
- Hacker Search Tools
- Nsa Hack Tools Download
- Hack Tools Download
- Pentest Tools Windows
- Hacking Tools Download
- Hacker Tools Free
- Hacking Tools Pc
- Hacking Tools For Mac
- Hacking Tools 2019
- Hacking Tools For Windows 7
- Pentest Tools Free
- Hacker Tools For Pc
- Tools Used For Hacking
- Nsa Hack Tools Download
- Nsa Hack Tools Download
- Hacker Tools For Pc
- Hacker Tools Linux
- Hacking Tools Windows 10
- Hacker Tools Free Download
- Underground Hacker Sites
- Hak5 Tools
- Hacking Tools For Mac
- Pentest Automation Tools
- Hacker Tools Software
- Hacking Tools Hardware
- Pentest Automation Tools
- Pentest Tools Github
- Hack Tools For Games
- Hackers Toolbox
- Game Hacking
- Pentest Tools List
- Pentest Tools Tcp Port Scanner
- Kik Hack Tools
- Install Pentest Tools Ubuntu
- Pentest Tools Website
- Hacking Tools 2019
- Hack Tools Pc
- Best Hacking Tools 2019
- Hack Apps
- Hack Tool Apk
- Computer Hacker